The STOP-IT project has released a number of research results, including tools, technologies, best practice guidelines, reports, materials, and an integrated STOP-IT platform with modular components. You find most of our downloads here or when you click on the boxes below.
The STOP-IT platform
Secure your water infrastructures against cyber-physical attacks and threats with the STOP-IT platform, which supports strategic/tactical planning, real time operational decision making and post-action assessment for the key parts of the water infrastructure. It is:
- scalable (scaling from small utilities to large ones)
- adaptable (including various modules addressing different needs, with expandability for future modules) and
- flexible (the water utility managers can decide how to use it and it will be usable by experts, novices, and even non-technical staff.
The main added value of the platform is that all modules and tools are integrated, connected to each other and interoperable, therefore ensuring the protection against combined cyber-physical threats and allowing the analysis of cascading effects of physical and cyber events. The platform was validated in an operational environment and all solutions were demonstrated in real environments.
The core modules (dark blue) form the backbone while the remaining cyber and physical modules (light blue) offer additional protection or information to critical infrastructure operators.
This video explains the workflow of the STOP-IT platform
You are currently viewing a placeholder content from YouTube. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
The tools of the STOP-IT platform
MODULE 1 - Strategic and tactical decision making tools
Module 1 includes 11 tools:
Risk Analysis and Evaluation Toolkit (RAET)
Risk Identification Database (RIDB)
InfraRisk (CP)
Asset Vulnerability Assessment Tool (AVAT)
Scenario Planner (SP)
Cyber-physical threats Stress-Testing Platform (STP)
Key Performance Indicators tool (KPI Tool)
Risk Reduction Measures Database (RRMD)
Water Quality Sensor Placement (WQSP)
Risk Exploration Tool (RET)
Epanet – EasySketch (EES)
Risk Analysis and Evaluation Toolkit (RAET)
This is a standalone toolkit. Download the following factsheet for more information:
| Description of the solution | A platform for identifying, analysing and evaluating cyber-physical risks and assorted mitigation actions by providing access to specific tools and models. The Risk Analysis and Evaluation Toolkit links interdisciplinary approaches into a seamless workflow, to synthesize actionable intelligence and support informed decision making in an interactive mode. |
| Challenges addressed | Converging cyber and physical security, assessing cyber-physical threats, and subsequently preparing against them can be a daunting task that requires multidisciplinary approaches and information from multiple sources that span from expert judgment to state-of-art models. There is a need for a system with integrative and modular architecture, that unifies cyber and physical security approaches for contemporary critical infrastructures under a common, flexible, and scalable platform. |
| Innovation | The RAET forms an innovative all-in-one solution that aids risk managers and strategic planners in cyber-wise water utilities. The innovations of the platform lay in each of the components. Thus, the toolkit acts as a wrapper for the nested cyber-physical simulation tools, simplifying and unifying the way the users interact with them. Results can be further explored through embedded components that help utilities to better understand and evaluate the scenario outcomes, based on the organization’s risk criteria. |
| Download or further information | Youtube-Video about RAET and further downloads. There also is a recorded webinar about the RAET toolkit approach and last, but not least, the link to the Risk Analysis and Evaluation Toolkit homepage. |
| Contact | Christos Makropoulos (Christos.Makropoulos@kwrwater.nl) George Karavokiros (george@itia.ntua.gr) |
The Risk Analysis and Evaluation Toolkit homepage
Risk Identification Database (RIDB)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Risk Identification Database is a list of risk events, e.g. examples that assist the users in the Risk Identification step, allowing them to commence the process and draw their attention to some possibilities that should be investigated. Risk events are related to physical and/or cyber threats, which can occur in water distribution systems/water utilities. The Risk Identification Database identifies the type of threat, the sources of risk, the description of the events and the type of consequences produced. |
| Challenges addressed | The tool highlights threat possibilities that should be investigated and their interrelated connections, which indicate that an event might occur. |
| Innovation | This is a new comprehensive database for physical and cyber threats on water distribution systems. |
| Download or further information | Further downloads: The Risk Identification Database – Excel File and Risk Identification Database – supporting document. |
| Contact | Elad Salomons (eladsa@technion.ac.il) Avi Ostfeld (ostfeld@cv.technion.ac.il) |
InfraRisk (CP) application
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | InfraRisk-CP is a generic risk assessment standalone desktop application devoted to assist in identification and prioritization of cyber-physical threats (CP) attacking the water systems. InfraRisk-CP is independent of any network modelling of systems (EPANET). Having in mind the so-called Bow-Tie visualization of risk, it starts out with a scenario and the undesired main events/threats, which are cyber-physical attacks against assets. The analysis differentiates between these cyber-physical threats, the frequency of main events and possible consequences, and finally, the preventive or protecting barriers. Barriers appear as physical assets or societal critical functions (SCF) in this context. By providing a risk picture presented as different risk matrices, the tool supports decision makers on both, tactical and operational levels in a user-friendly manner. |
| Challenges addressed | Generic risk assessment of cyber-physical threats to water systems. |
| Innovation | Market interest and potential for this tool are high. The tool could be commercially exploited within one year. Innovation readiness and innovation management are scored medium. |
| Download or further information | The InfraRisk CP user guide |
| Contact | Eivind H. Okstad (Sintef): eivind.h.okstad@sintef.no Jørn Vatn (Sintef): jorn.vatn@ntnu.no |
Open window of InfraRisk-CP
Assessment with InfraRisk-CP
Asset Vulnerability Assessment Tool (AVAT)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Asset Vulnerability Assessment to Risk Events (AVAT) tool is acting as a procedural „step-by-step“ guide for the assessment of vulnerability of water distribution system assets, taking into consideration the specific characteristics of the assets, the importance of the components for water supply and their „attractiveness“ to be attacked. |
| Challenges addressed | AVAT shows the criticality of each element in the water network, using vulnerability metrics. The tool helps to handle the complexity of water distribution networks, where usually it is not trivial to gain knowledge on the location of the vulnerable components. The tool can score different configurations of the network. |
| Innovation | AVAT allows for quick and simple evaluation of the network vulnerability, which helps the user to focus on the most critical elements, without going through the usual time consuming activities. |
| Download or further information | Supporting document |
| Contact | Elad Salomons (eladsa@technion.ac.il) Avi Ostfeld (ostfeld@cv.technion.ac.il) |
Visualization of results with AVAT
Scenario Planner (SP)
This tool is integrated in the the Risk Analysis and Evaluation Toolkit. Download the following factsheet for more information:
| Description of the solution | The Scenario Planner is an intuitive scenario planning environment to specify multiple-threat scenarios by guiding through available fault trees and mitigation options. It generates model-specific data according to the formulated scenario and passes it to the embedded cyber-physical solvers. |
| Challenges addressed | Simulation models are powerful, yet often difficult tools to work with. The Scenario Planner helps the user to decide which threats to be examined using an intuitive graphical interface. It also enables the user to build scenarios of their interest in order to be examined and simulated within the STOP-IT Stress Testing Platform or any other supported model. |
| Innovation | By employing the Scenario Planner, a higher level of abstraction is provided to the end user, hiding the underlying data files needed by a model to run the simulation. In most cases, the user has to develop the base scenario from scratch only once and then the SP guides them to define attack scenarios, i.e. variations to the base scenario. |
| Download or further information | Supporting document |
| Contact | Christos Makropoulos (Christos.Makropoulos@kwrwater.nl) George Karavokiros (george@itia.ntua.gr) |
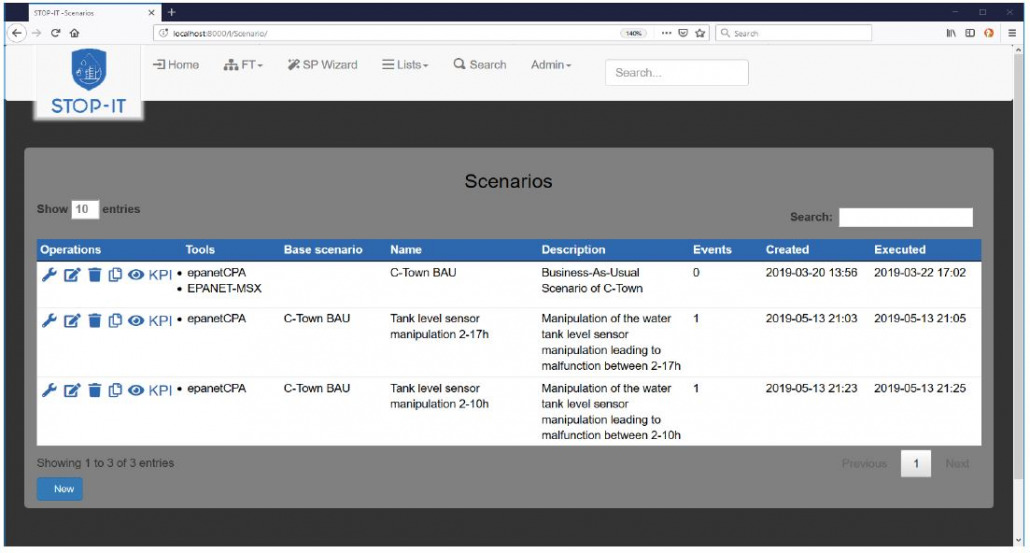
Scenario Planner listing page
Cyber-physical threats Stress-Testing Platform (STP)
This tool is integrated in the the Risk Analysis and Evaluation Toolkit. Download the following factsheet for more information:
| Description of the solution | A powerful feature of the Risk Analysis and Evaluation Toolkit (RAET) is the Stress Testing Platform (STP), enabling users to run in a batch procedure multiple variations of a given scenario, similarly to a sensitivity analysis approach. In fact, the STP turns all numerical parameters of events comprising a scenario, such as event duration, leakage area or mass of pollutant, into control variables of a stress testing procedure. Users are able to set a value range for each parameter and specify the number of values and the sampling method |
| Challenges addressed | After the identification of a potential cyber-physical threat, risk managers and utility personnel are facing the challenge of estimating the severity of such a situation and the conditions under which the threat would have its greatest impact. This time consuming process includes the execution of multiple scenario simulations, defined by experts, with the inherent risk of missing an important scenario variation. |
| Innovation | The STP will automatically create scenarios having unique combinations of parameter values according to the specifications of the risk manager and will successively execute simulations in a single, seamless stress testing procedure. Managers can control the procedure and view the results as they emerge. |
| Download or further information | Supporting document |
| Contact | Christos Makropoulos (Christos.Makropoulos@kwrwater.nl) George Karavokiros (george@itia.ntua.gr) |
A stress testing scenario
Key Performance Indicators tool (KPI Tool)
This tool is integrated in the the Risk Analysis and Evaluation Toolkit. Download the following factsheet for more information:
| Description of the solution | The KPI tool is a MATLAB®-based standalone executable, designed to assist in the evaluation process of a threat scenario of cyber and physical attacks. As a whole, the Key Performance Indicator Tool enhances the single scenario assessment, allowing the users to select scenario results and a number of configurations of the system to create a deeper analysis of the simulation results, and identify key information for the tactical and strategic planning. |
| Challenges addressed | The results produced from a simulation process can be huge and/or difficult to interpret. They are usually provided in form of large textiles, documenting the results in detail in the temporal and spatial dimension. There is often a need for supporting graphical and user-friendly tools that would help professionals to easily identify security critical information. The aim of the tool is not to export any ranking or final decision on criticality of a threat, but rather present a user-friendly environment to deploy the STOP-IT Key Performance Indicator Framework in a structured way. |
| Innovation | The main concept behind the KPI tool is a sequential application of user-defined selections as filters to visually present only selected parts of consequence information. The adjustability of the Key Performance Indicators to the company’s risk attitude is the main pillar of the tool development, while additional functionalities were added to assist the risk informed decisions for the threat scenarios examined. All results are presented in a unified way, regardless of the underlying model from which they have been produced. |
| Download or further information | Supporting document |
| Contact | Christos Makropoulos (Christos.Makropoulos@kwrwater.nl) George Moraitis (georgemoraitis.gm@gmail.com) |
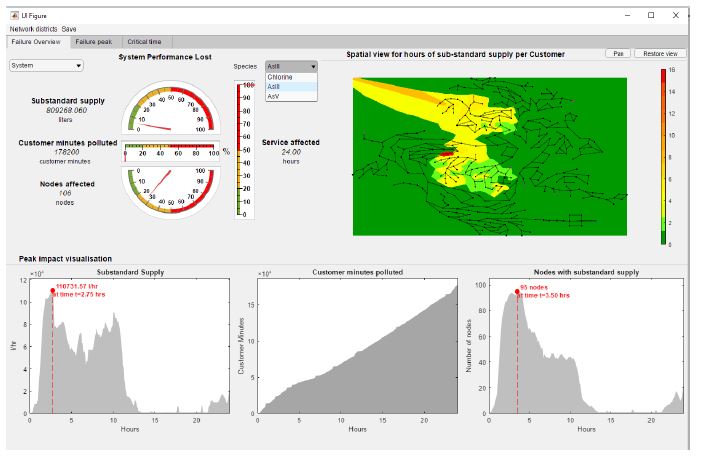
Results visualization of the Key Performance Indicator Tool
Risk Reduction Measures Database (RRMD)
This is a standalone tool but can be used in combination with the Risk Identification Database (RIDB) and the Risk Analysis and Evaluation Toolkit. Download the following factsheet for more information:
| Description of the solution | The Risk Reduction Measures Database is a collection of mitigation measures that helps to establish a strategy for the minimization of the effect of materialization of risks inside the water critical infrastructure. It is related to the identified risks of the Risk Identification Data Base (RIDB). |
| Challenges addressed | The collection and categorization of possible risk reduction measures and the development of a method and an algorithm for the automatic link between the identified risks and possible risk reduction measures. |
| Innovation | Suitable risk reduction measures are automatically identified for a selected risk. The user can search the RRMD for measures through the functionality provided by the Risk Analysis and Evaluation Toolkit: a) by performing a full text search upon all descriptive fields of the RRMD, giving a single keyword or a combination of keywords to search and b) by filtering out suitable measures through the advanced search form of the RAET, combining search criteria from all data categories of the RRMD. |
| Download or further information | Download the RRMD database here and the supporting PDF document here. |
| Contact | Hans-Joachim Mälzer (IWW): a.maelzer@iww-online.de Aitor Corchero (Eurecat): aitor.corchero@eurecat.org |
The Risk Reduction Measures Database
Water Quality Sensor Placement Tool (WQSP)
This is a standalone tool but since it does not have a visual interface, it is better to be connected with the XL-SIEM tool. Download the following factsheet for more information:
| Description of the solution | The Water Quality Sensor Placement (WQSP) tool helps water utilities to place water quality sensors to establish a warning system against water contamination network intrusions. |
| Challenges addressed | The tool provides information to assist decision makers in sensor station locations, the trade-off between the number of sensors and impact measures and the evaluation of the impact of existing sensor stations. |
| Innovation | The tool provides data to evaluate sensor failures (e.g. due to a cyberattack). |
| Download or further information | Further downloads and here is a video about the WQSP on Youtube. |
| Contact | Elad Salomons (eladsa@technion.ac.il) Avi Ostfeld (ostfeld@cv.technion.ac.il) |
Risk Exploration Tool (RET)
This tool needs to be connected with the Risk Identification Database (RIDB), the Risk Analysis and Evaluation Toolkit. and the Risk Reducation Measures Database. Download the following factsheet for more information:
| Description of the solution | The Risk Exploration Tool permits to explore the risks and mitigation actions using the semantic-enriched information, called facets, which allow to homogenise the information under a common vocabulary, and subsequently, provide interoperability between digital systems using a common data format, namely JSON-LD. Considering the risk management domain, one of the main advancements corresponds to the publication of a risks and mitigation actions catalogue to facilitate managers in critical infrastructures to organise the risk management plan. Specifically, the tool offers the possibility to link risks with corresponding risk reduction measures and provides information on the potential implications in case risks would ever be realized. |
| Challenges addressed | Semantic interoperability is the main goal of making information machine-readable by giving them unambiguous, shared meaning. Numerous semantic models exist representing digital and physical systems and linking them with operations accessing the data. However, cyber-physical threats in water infrastructures have not been studied yet in an integrated approach extensively. Therefore, there is a lack of interoperability and data sharing in systems responsible for risk management at the operational, tactical, and planning levels. |
| Innovation | Based on a systematic approach, a representation of concepts, data and entities describing water infrastructures and related cyber-physical threats has been defined, partly by combining and reusing existing ontologies in related fields. The resulting new ontology allows data of cyber and physical threats in water infrastructures to be shared and reused across application, enterprise, and community boundaries without prior knowledge of the data structure, taking advantage of the semantic relation between the defined terms. |
| Download or further information | The RET is described in the Risk Assessment and Treatment Framework here. |
| Contact | Aitor Corchero (aitor.corchero@eurecat.org) Christos Makropoulos (Christos.Makropoulos@kwrwater.nl) |
Risk Exploration Tool backend Open-API (Swagger)
EPANET – EasySketch (EES)
This tool is standalone, available in the the Risk Analysis and Evaluation Toolkit. Download the following factsheet for more information:
| Description of the solution | In case that a water company has no pipeline network model, the Epanet – EasySketch (EES) tool is used to generate an EPANET input file starting from a simplified sketch of the system without use of the EPANET software. |
| Challenges addressed | The access to the modelling platform of STOP-IT and the use of the tools of this platform is only possible for water companies, who already have a model of the pipeline network. To overcome this requirement and in case that a water company has no pipeline network model, the Epanet – EasySketch (EES) tool can be used. |
| Innovation | The tool may be used when (a) calculations based on an EPANET model are performed, (b) a calibrated hydraulic network model is not available, (c) the typical setup of a hydraulic model is too sophisticated for the desired results, (d) the water supply company has not the skilled and trained staff, and (e) rough estimations are sufficient. |
| Download or further information | Download |
| Contact | Hans-Joachim Mälzer (a.maelzer@iww-online.de) Maxim Juschak (m.juschak@iww-online.de) |
Epanet tool: Scheme of a supply system with EasySketch
MODULE 2 - Tool to detect and inform about wireless jamming attacks
Module 2 includes 1 tool, the Jamming detection sensor (Jdet)
Jamming Detection Sensor (JDet)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Jammer detector solution performs detection of physical disturbances of wireless communications to ensure that they are not compromised by Denial of Service (DoS). The Jammer detector detects anomalies on the wireless communication physical layer and informs when there is a jamming attack. It also allows the detection of different types of jamming, logs and communicates the type of jammer, its strength, timestamp and frequency. |
| Challenges addressed | Real-time detection of jamming attacks in wireless communication to improve the security at physical level. |
| Innovation | Real-time detection supports the identification of jammer attacks, which block wireless communications. The jammer detector supports the actual identification of jammer attacks and sends alerts that facilitate taking corrective action quickly. |
| Download or further information | Watch this video about the Jammer Detector on Youtube. |
| Contact | Ignasi Garcia-Milà (Worldsensing): igarciamila@worldsensing.com Maite Garcia (Worldsensing): mgarcia@worldsensing.com |
Network view for Jamming attack sensors
Example of an installed sensor (not fixed to a wall but using a tripod, which is another option)
Jammer detector capable of blocking signals at 2.4GHz band
MODULE 3 - Tools to monitor and protect SCADA and IT systems
Module 3 includes 3 tools:
Network Traffic Sensors and Analysers (NTSA)
Real-time sensor data protection (RSDP)
Fault-tolerant Control Strategies for Physical Anomalies affecting the SCADA system (FTCS)
Factsheet: Fault-tolerant Control Strategies for Physical Anomalies (FTCS)
Network Traffic Sensors and Analysers (NTSA)
This is a standalone tool but since it does not have a visual interface, it is better to be connected with the XL-SIEM tool. Download the following factsheet for more information:
| Description of the solution | The Network Traffic Sensors and Analysers (NTSA) tool uses machine algorithms to build a model of the regular behaviour associated to a critical water infrastructure, based on NetFlow traffic data. The model is used to detect abnormal network traffic behaviour in real time and performs an analysis of the NetFlow traffic data generated by routing and switching devices to detect anomalous behaviours and attacks. By analysing the data provided by NetFlow, a network/security administrator is able to identify useful information about the network traffic. |
| Challenges addressed | Real-time detection and the development of a model representing the regular behaviour of critical water infrastructure. |
| Innovation | The main innovation of this technology covers the real-time detection of abnormal behaviour of the network traffic in a SCADA infrastructure. |
| Download or further information | Publication: LADS: A Live Anomaly Detection System based on Machine Learning Methods. You also will find information about the NTSA tool at the Toolbox for IT and SCADA security and there is an explanatory video about the NTSA on Youtube. |
| Contact | Gustavo Gonzalez (Atos): gustavo.gonzalez@atos.net Rodrigo Diaz (Atos): rodrigo.diaz@atos.net |
NTSA Architecture
Real-time Sensor Data Protection (RSDP)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Real-Time Sensor Data Protection (RSDP) tool is based on Blockchain technology and provides a mechanism to guarantee the integrity of data generated within the critical-infrastructure operation (principally sensor data), both against intentional attacks or malfunctions. The Real-Time Sensor Data Protection tool guarantees the integrity of the stored data. Customers will be able to detect data modifications (or corruption) of data in transit from the end-points (sensors) where the data has been collected (or generated) to the time it is being stored in their storage systems. |
| Challenges addressed | This tool guarantees the integrity and immutability of data, being able to detect the tampering (intentionally or accidentally) of the data generated mainly by sensors and field devices in critical infrastructures. |
| Innovation | The application of Blockchain technology guarantees the integrity of data gathered from electronic devices and stored in the system in a decentralized way. |
| Download or further information | Watch this video about the Real-Time Sensor Data Protection (RSDP) tool on Youtube. You also will find more information about the RDSP tool at the Toolbox for IT and SCADA security. A description relating how the proof of integrity of the data is generated using a hash function over the stored data can be found on Wikipedia. |
| Contact | Juan Caubet (juan.caubet@eurecat.org) Mario Reyes (mario.reyes@eurecat.org) |
Simplified schema of the service during upload
Fault-tolerant Control Strategies for Physical Anomalies affecting the SCADA system (FTCS)
This is a standalone tool but it needs two external commercial tools (check requirements on the factsheet). Download the following factsheet for more information:
Factsheet: Fault-tolerant Control Strategies for Physical Anomalies (FTCS)
| Description of the solution | The tool Fault-tolerant Control Strategies for Physical Anomalies affecting the SCADA system optimizes the transport network reconfiguration to minimize the impact of anomalies affecting the integrity of the network assets and, therefore, the supply of the existing water demand. |
| Challenges addressed | The challenges addressed are to mitigate the impact of a partial shutdown of the water network due to either planned interruptions (i.e. periodic maintenance) or due to unexpected events (i.e. pipe burst), and to support water operators to choose the interventions to be applied in the network in order to guarantee a fast recovery of the water supply services. |
| Innovation | The innovation consists of a simulation environment based on integrating the network hydraulic model with an optimization framework. |
| Download or further information | Watch this video about the FTCS tool on Youtube. You also will find more information about the RDSP tool at the Toolbox for IT and SCADA security. Here you can find the General Algebraic Modelling System (GAMS) software. |
| Contact | Susana González (sgonzalez@cetaqua.com) Jordi Meseguer (jmeseguer@cetaqua.com) |
Functional scheme
MODULE 4 - Tools for protection against physical threats
Module 4 includes 4 tools:
Computer Vision Tools (CVT)
Access Control System using Electronic Locks (Smart-Locks)
Human Presence Detection using WiFi signals (HPD)
Fine-grain Cyber Access Control (FCAC)
Computer Vision Tool (CVT)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Computer Vision Tool (CVT) provides an automatic assessment of actions and behaviours caught on camera. The tool creates a model that can utilise inputs from multiple cameras, thermal cameras, and even other sources of information, and can detect (classify) movements as normal. |
| Challenges addressed | Automated detection of abnormal behaviour using video cameras. The abnormality is modelled based on a specific video stream and its usual contents. |
| Innovation | An algorithm that can provide information based on the current video stream, without any issues with migration to different streams. |
| Download or further information | Watch this video about the Computer Vision tool on Youtube and find further information in our toolbox for protection against physical threats. An overview of the proposed model, as well as the weights of the proposed system, can be found on ZENODO here. |
| Contact | Nikos Bakalos (bakalosnik@mail.ntua.gr) Athanasios Voulodimos (thanosv@mail.ntua.gr) Anastasios Doulamis (adoulam@cs.ntua.gr) |
Architecture of the proposed Deep-NARMA Filter
Access Control System using Electronic Locks (Smart-Locks)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Smart Locks are an Access Control System based on the use of electronic locks and a mobile App, directly connected to the SCADA systems. The Smart-Locks provide users the ability to arm and disarm the security systems on the sites on demand. They allow to centralise the access requests, automating the process of granting access to specific areas within the same site, as well as to give access for limited time. Authorized users receive an electronic key and an access-control mobile app. Access points are equipped with stand-alone smart electronic locks. These locks communicate with the authentication and back-end servers via the authorized user‘s mobile application. The system needs the location of the site, maps and the information on the workers in the site that will need access privileges. All the data can be controlled easily from the management system. |
| Challenges addressed | With the help of the system it is possible to track entry of authorized users or enable or disable remote privileges for opening and locking doors. It does not require the implementation of wired or wireless infrastructure and therefore reduces maintenance costs. It increases the safety, is user friendly and flexible, offers navigation to facilities and works with a standalone system, among other things. |
| Innovation | Meklock is an innovative smart lock access-control mobile app with a sophisticated management system that interacts with electronic locks and integrates with electronic locking devices. It also is possible to track entry of authorized users and lock doors remotely. It consists of two main parts, a management system that controls the data of the company and from the site (remote sites, alarms, app requests, permissions, users, dynamic maps, smart locks, site codes, etc ), and a mobile application for the end users. |
| Download or further information | You can find a video about the Meklock system on Zenodo here and on Youtube here. You also will find out more about the tool at the Toolbox for protection against physical threats. |
| Contact | Saar Afuta (Aplicatzia): saar@aplicatzia.com |
Overall Smart Locks system architecture
Human Presence Detection using WiFi signals (HPD)
This is a standalone tool. Download the following factsheet for more information:
Here you can download the User Guide for the Human Presence Detector:
| Description of the solution | The Human Presence Detector using WiFi signals (HPD) is a detector of people moving in a delimited area just by processing the signals generated by at least one commercial WiFi device. This system requires no special hardware to be deployed and is easy to set up with a simple training process. |
| Challenges addressed | It is an easy to deploy and configure detection system, inexpensive and non-intrusive to people’s privacy. It works in the absence of light and through walls. |
| Innovation | The use of WiFi signals generated by at least one commercial WiFi device to detect the movement of a person, allowing to take advantage of WiFi networks already deployed in the critical infrastructures. |
| Download or further information | You will find more information about the HPD on Zenodo, on Youtube and at the toolbox for protection against physical threats. |
| Contact | Juan Caubet (Eurecat): juan.caubet@eurecat.org Mario Reyes (Eurecat): mario.reyes@eurecat.org Víctor Jiménez (Eurecat): victor.jimenez@eurecat.org |
Human Presence Detector installed in a small office area
Fine-grain Cyber Access Control (FCAC)
This is a standalone tool but since it does not have a visual interface, it is better to be connected with the XL-SIEM tool. Download the following factsheet for more information:
| Description of the solution | The Fine-grain Cyber Access Control (FCAC) employs user specified policies to determine who can access which resources and for what purpose. This tool evaluates authorization requests for users of the STOP-IT platform and provides rules to be implemented by cyber and/or physical security devices. |
| Challenges addressed | The correlation of cyber and physical access violations and the real time detection of access control violations in a critical water infrastructure. |
| Innovation | Main innovations of this technology are in the context ofvscalability, simplification of the device/user management, multi-stakeholder (able to deal concurrently with different access policies), support of authorization delegation and rights revocation. |
| Download or further information | You will find out more about the tool at the Toolbox for protection against physical threats. |
| Contact | Gustavo Gonzalez (Atos): gustavo.gonzalez@atos.net Rodrigo Diaz (Atos): rodrigo.diaz@atos.net |
Fine-grained Cyber Access Control (FCAC) Architecture
MODULE 5 - Tool storing and sharing information about cyber threats and attacks across critical infrastructure
Module 5 includes 1 tool, the Cyber Threat Incident Service (CTSS)
Cyber Threat Sharing Service (CTSS)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The Cyber Threat Sharing Service (CTSS) collects and shares information about known threats and incidents that could affect critical infrastructures. CTSS is collecting sources of existing threats from relevant feeds, and structuring the information using standards to facilitate the exchange of the security threats identified (e.g. MITRE, OASIS). Personalized alerts and relevant information will be provided according to the subscription parameters the critical infrastructure has requested. This service will ensure the mitigation of threats to critical infrastructure; will enhance the coordination within critical infrastructure establishing exchange methods to prevent, reduce, mitigate and recover from existing threats; and will allow the coordination between similar centres in the world to deal with critical infrastructure threats in a global approach. |
| Challenges addressed | The sharing of information on threats and attacks in the water domain, and the generation of knowledge (threat & security intelligence) from this information. |
| Innovation | The use of standard protocols of information sharing in cybersecurity and the use of machine learning algorithms to generate advanced security knowledge (threat & security intelligence). |
| Download or further information | Here is a further download and there is video on Youtube about the CTSS and another one on Zenodo. |
| Contact | Juan Caubet (juan.caubet@eurecat.org) Mario Reyes (mario.reyes@eurecat.org) |
Cyber Threat Sharing Service architecture
MODULE 6 - Tools to detect cyberphysical anomalies
Module 6 includes 2 tools:
Real-Time Anomaly Detector (RTAD)
Cross Layer Security Information and Event Management (XL-SIEM)
Factsheet: Cross Layer Security Information and Event Management (XL-SIEM)
Real-Time Anomaly Detector (RTAD)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The tool provides real time anomaly detection for cyber-physical infrastructures based on the use of machine learning algorithms. There is an additional layer of security by detecting complex and combined potential threats and attacks. The tool is composed of three main components: a security Big Data platform, machine learning algorithms, and signature-based rules. |
| Challenges addressed | The detection of unknown attacks (0-days), customised and targeted attacks (Advanced Persistent Threats) as well as complex and combined attacks in a critical water infrastructure. |
| Innovation | The differentiation factor with other tools in the market that use machine learning algorithms to detect unknown anomalies (complex and combined threats and attacks) is the ability and flexibility to integrate different sources of information, both cyber and physical, which increases the efficiency and performance of the solution. |
| Download or further information | STOP-IT tool explained on Youtube: The Real Time Anomaly Detector |
| Contact | Juan Caubet (Eurecat): juan.caubet@eurecat.org Mario Reyes (Eurecat): mario.reyes@eurecat.org Alexis Sánchez (Eurecat): alexis.sanchez@eurecat.org |
The Real Time Anomaly Detector
Cross Layer Security Information and Event Management (XL-SIEM)
This is a standalone tool but it needs at least one security sensor (check requirements in the factsheet). Download the following factsheet for more information:
Factsheet: Cross Layer Security Information and Event Management (XL-SIEM)
| Description of the solution | This tool receives cybersecurity events coming from different sources (e.g. firewall, honeypot) to generate correlated alarms that indicate the risk level, and give detailed information about the event (description, IP source and destination, port source and destination, protocols). The tool can generate tickets for further investigation. |
| Challenges addressed | The correlation of cyber and physical events originated in water critical infrastructures and the detection of attacks against water critical infrastructures in real time. |
| Innovation | Main innovations of this technology are in the context of (i) scalability: events processed in parallel across a cluster of nodes; (ii) resilience: fault-tolerant and automatic reassignment of task; and (iii) expressiveness: capacity to define rich correlation rules from different perspectives. |
| Download or further information | Find here a publication about the XL-SIEM. |
| Contact | Gustavo Gonzalez (Atos): gustavo.gonzalez@atos.net Rodrigo Diaz (Atos): rodrigo.diaz@atos.net |
XL-SIEM High Level Architecture
MODULE 7 - Tool for alerting users/citizens about a critical situation
Module 7 incudes 1 tool, the Public Warning Notification System (PWNS)
Public Warning Notification System (PWNS)
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The STOP-IT Public Warning Notification System detects incidents and informs users and citizens by sending information and instructions to follow. The PWNS has two main functionalities: detect and report incidents, and inform users and citizens. It is a key element in the solution developed by the STOP-IT project as it activates the first phase of the system, triggering an alert that will ultimately put in place the corresponding response plan. |
| Challenges addressed | Water agencies, regulators, municipalities and environmental agencies can benefit from the Public Warning Notification System. The tool is also useful for any industrial operator who needs to monitor processes and can integrate data sources or deploy sensors to capture data variables. Such data can be processed to generate alerts when specific conditions, like threshold limits, absolute/relative variations or other rules upon request from the operator, are met. Response plans and lists of action to be taken when a specific situation is presented can be defined individually to enable the operator to implement the appropriate actions. |
| Innovation | The PWNS processes data, alerts and detected incidents from external sources and reports them to the STOP-IT core platform. At this initial stage the incident has to be validated by a human operator. Once this is done, the anomaly is notified to the system that, by cross-checking with other incident-related data from different sources, can identify the risk situation. This assessment will be sent to the visualisation interface for water utilities. The visualisation interface starts a response plan with actions to be executed when specific situations arise. These actions are based on different parameters set by water operators and can include both, corrective and mitigation measures. The system also sends the information and instructions to follow to the users and citizens using the most appropriate channels, i.e. email, SMS, mobile app notifications, etc. |
| Download or further information | Find more about the Public Warning Notification System here. The tool is available at Zenodo and the source code at Github. |
| Contact | Ignasi Garcia-Milà (Worldsensing): igarciamila@worldsensing.com Maite Garcia (Worldsensing): mgarcia@worldsensing.com |
MODULE 8 - Tools for risk exposure assessment, alert generation and countermeasure proposition
Module 8 includes 2 tools:
Reasoning Engine (REN)
Fault Tree Editor (FTE)
Reasoning Engine (REN)
This tool needs to be connected to the Real-time Anomaly Detector (RTAD). Download the following factsheet for more information:
| Description of the solution | The reasoning engine generates real-time alerts and proposes mitigation actions. It allows the configuration of rules for processing detections (referring to cyber and physical level) and generates high-level alerts by using Complex Event Processing (CEP). Subsequently, it provides mitigation actions to be taken and extra information that facilitates the operators. The Reasoning Engine acts as a mediator between event sources and the system operator and is the means to filter, aggregate, correlate and upscale information in an endless stream of input data. |
| Challenges addressed | With real-time alerting and mitigation proposition, the tool supports the decision-making process in water utilities. Based on the Reasoning Engine’s reactive and asynchronous reasoning principle, it detects patterns in an endless stream of input data, allowing the selection of important information. The operator on duty is facilitated and can be less experienced/trained, compared to traditional practice. Regarding the mitigation of incidents, the tool, in compliance with the MITRE ATT&CK framework, includes tactics and techniques to the advice on how to mitigate the received events to speed up investigations and responses. The tool also supports batch-processing, vital for post-evaluation and further enhancement of the processing results. |
| Innovation | The tool allows configurable processing per water utility that involves cyber and physical events as it integrates with the rest of the tools in the STOP-IT platform. |
| Download or further information | You will find related information here. |
| Contact | Theodora Karali (Risa): d.karali@risa.de Stephanos Camarinopoulos (Risa): s.camarinopoulos@risa.de |
Configuration of a processing rule
Fault tree editing
Fault Tree Editor
This is a standalone tool. Download the following factsheet for more information:
| Description of the solution | The solution assesses the risk exposure of a water utility with the creation and calculation of Fault Trees. A Fault Tree is a systematic and deductive method for defining a single undesirable event and determining all possible reasons that could cause that event to occur. It can be applied to analyse the combined effects of simultaneous failures on the undesired (top) event, to evaluate system reliability, to identify potential design defects and safety hazards, to simplify maintenance and troubleshooting and finally it can also be used to evaluate potential corrective actions or the impact of design changes. |
| Challenges addressed | Addressed is the need of water utilities for tactical and strategic decisions and planning. In particular, the methodology provides all the tools needed to represent, quantify and understand the risks involved in the utility. Moreover, it provides a reliable basis for determining safety countermeasures, in order to predict, prevent or mitigate accidents. |
| Innovation | The implemented methodology is quite flexible and can analyse the consequences caused by some units and special reasons resulting in accidents, such as human factors and environmental factors. A treatment of Common Cause failures and a subset of the general set of dependent events having a significant contribution on the safety of technical systems are implemented in the method. |
| Download or further information | Find out more about the Fault Tree Editor within the information about the Reasoning Engine. |
| Contact | Stephanos Camarinopoulos (Risa): s.camarinopoulos@risa.de |
Fault Tree Editor
MODULE 9 - Tool that visualises information in the STOP-IT platform from all modules
Module 9 includes 1 tool, the Enhanced Visualisation Interface for the water utilities (EVI)
Factsheet: Enhanced Visualisation Interface for the water utilities (EVI)
Enhanced Visualisation Interface for the water utilities (EVI)
This tool needs to be connected to at least one of the following tools: Reasoning Engine (REN), Real-time
Anomaly Detector (RTAD), Computer Vision Tool (CVT) and/or the Public Warning Notification System (PWNS). Download the following factsheet for more information:
Factsheet: Enhanced Visualisation Interface for the water utilities (EVI)
| Description of the solution | Purpose of the Enhanced Visualization Interface is to share operational information for the understanding of the current situation in a water utility. It is a web user interface that enhances situational awareness by creating a common operational picture. The module leverages real-time, historical and GIS mapping data, incident information and shared information and displays them in multiple-perspective views. The information can be simultaneously shared among operators and decisionmakers during all phases of risk management, detection, processing, analysis and mitigation, allowing collaboration for cyber and physical incidents. |
| Challenges addressed | Operators and decision makers can simultaneously view data from multiple sources to understand the current situation in a water utility and act effectively. To avoid overloading users with information, the interface is organised in multiple views. The module is scalable from small utilities to large ones with multiple water distribution networks, it can be expanded to consume information from other external modules and it is flexible, allowing water utility managers to decide its use by experts or non-technical staff. |
| Innovation | The solution brings together the cyber and physical worlds and all phases of risk management: From the detection, processing and analysis to the corresponding mitigation. |
| Download or further information | Find out more about EVI here. |
| Contact | Theodora Karali (d.karali@risa.de) Stephanos Camarinopoulos (s.camarinopoulos@risa.de) |
Temporal distribution of alerts
The STOP-IT platform.
The STOP-IT platform can be connected to all other tools and modules. Download the following factsheet for more information:
Factsheet about the STOP-IT platform
| Description of the solution | Secure your water infrastructures against cyber-physical attacks and threats with the STOP-IT platform, which supports strategic/tactical planning, real time operational decision making and post-action assessment for the key parts of the water infrastructure. The STOP-IT platform is the combination of all STOP-IT tools in an integral, scalable, adaptable, flexible and modular solution. The main added value of the platform is that all modules and tools are integrated, connected to each other and interoperable, therefore ensuring the protection against combined cyber-physical threats and allowing the analysis of cascading effects of physical and cyber events. The platform was validated in an operational environment and all solutions were demonstrated in real environments. |
| Challenges addressed | STOP-IT solutions through their combination will help water utilities operators identify and detect risks, enhance their analysis capabilities as well as their preparedness and response. |
| Innovation | The STOP-IT platform introduces a novel integrated approach for the security of water critical infrastructures that combines cyber and physical protection modules in an overarching solution. |
| Download or further information | Find out more about the STOP-IT platform with this Youtube-Video. And here you will find some background material. |
| Contact | Project coordinator Rita Ugarelli (Sintef): Rita.Ugarelli@sintef.no Theodora Karali (d.karali@risa.de) Stephanos Camarinopoulos (s.camarinopoulos@risa.de) |
STOP-IT Modular components and Dataflow
The connection of the STOP-IT platform modules and tools
The Interoperable Water Middleware (which is an additional tool integrating all STOP-IT tools) is standalone but can be connected to all other tools and modules. Download the following factsheet for more information:
| Description of the solution | The STOP-IT interoperable water middleware is a web-based tool to access the information of the critical infrastructure and expose that information using a common data exchange model. Therefore, the interoperable water middleware corresponds to a context-broker model that follows the standards of NGSI-LD (compatibility with FIWARE) and also, with the Web of Things architecture (W3C standards). The combination of both systems enables STOP-IT to elaborate several “plugins” (COAP; MQT; REST) to interact with the different systems and uplift the information using the common vocabulary. |
| Challenges addressed | Commonly in the water infrastructure, there are different informational “siloes” that fragmented the sector. Moreover, the lack of data exchange models combined with the adoption of different standards caused a limited decision-making. For that, there is a need for digital tools that enable information interrelationships to share knowledge inside the water infrastructures. This aspect will enable new strategies to detect critical events. |
| Innovation | Based on the challenges exposed in the previous point, the main innovations performed with the middleware can be summarised into the elaboration of common data exchange model based on current standards (ontology) to represent and model risk and mitigation actions. Moreover, the adoption of open-standards such as NGSI and WoT enable to be compatible with FIWARE and WoT reference architectures. Thus, it will be an open framework compatible with EU and international digital architectures for integrating massive amount of data. |
| Download or further information | – |
| Contact | Aitor Corchero (aitor.corchero@eurecat.org) Xavier Domingo (xavier.domingo@eurecat.org) |
Open and standard API of the water middleware